Articles
Explanation of Secure System Startup Processes | Concurrent Technologies Processor Boards
.jpg)
Overview
There are a number of terms used to describe a secure system start up, each performs a slightly different task. Microsoft and Intel have been responsible for most of these terms, and they apply to booting Windows and non-Windows operating systems.
Initial Requirements
N/A
Startup processes available
Secure Boot
In conjunction with UEFI BIOS, a Root of Trust is created with the firmware to ensure that a known, certified boot loader is used to load the next stage loader/manager or O/S kernel. The boot process stops if the certificate does not match.
Trusted Boot
Trusted Boot is just really an extension of Secure Boot process and takes over from where Secure Boot finishes. The ‘boot manager’ again uses certificates to ensure it loads trusted O/S components. The boot process stops if a certificate does not match.
Measured/Verified Boot
Measured Boot is the process of measuring and storing securely (i.e. using a TPM) the next stage object in the boot process by the UEFI BIOS, boot loader, kernel, etc. The boot process is not stopped as there is no checking done at this stage.
Boot Guard
There is another early boot stage safe guard that Intel has also introduced in recent processor architectures (Haswell onwards) and that is called Boot Guard. This prevents the board from running firmware images not released by the system manufacturer. The processor verifies the signature contained within the firmware before executing it. If it fails, there is no hand off to the BIOS code. This is a ‘one time’ operation fused into the ‘processor’ by the hardware manufacturer, i.e. Concurrent Technologies. This creates a hardware/firmware Root of Trust.
All of the technologies rely on a “Root of Trust”, that is, some piece of code or hardware that’s been hardened well enough that it’s not likely to be compromised, and either can’t be modified at all, or else can’t be modified without cryptographic credentials. For many systems, that Root of Trust is provided by the Unified Extended Firmware Interface (UEFI) BIOS.
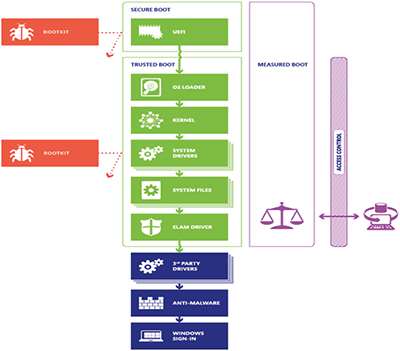
Figure: Secure/Trusted/Measured boot process (as defined by Microsoft)
What is Secure Boot?
Secure Boot is designed to add a layer of protection to the pre-boot process. With Secure Boot active, the firmware checks for the presence of a cryptographic signature on any UEFI program that it executes. If the cryptographic signature is absent or doesn't correspond to an entry in a database of valid keys held within secure variables of the UEFI BIOS, the firmware will refuse to execute the program and the boot process halts. Of course, this is simply the start of the process; a trusted EFI boot loader must continue the boot process in a secure fashion, leading ultimately to an OS that is itself secure.
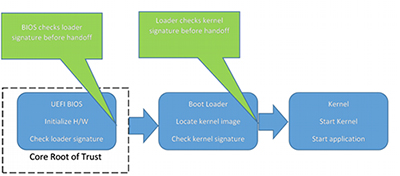
Figure: Secure Boot process
What is Trusted Boot?
As mentioned above, Trusted Boot is an extension of Secure Boot, in that it performs the same checks using cryptographic signatures. For a Windows system this would use the Boot Manager, where as a Linux based system this could be Shim, grub2 or tboot (available as UEFI executable and TPM 1.2/2.0 enabled). These all come with pre-built in Microsoft keys or a user can build their own version, with their own key.
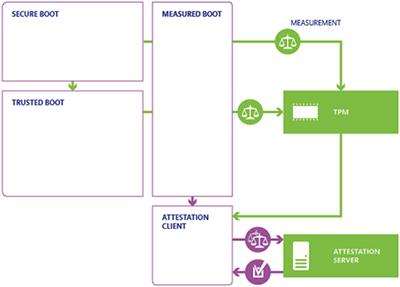
Figure: Where Trusted Boot fits in the startup process
What is Measure/Verified Boot?
Measured Boot still depends on a Root of Trust as the starting point for a chain of trust. But in this case, prior to launching the next object, the currently-running object “measures” or computes the hash of, the next object(s) in the chain, and stores the hashes in a way that they can be securely retrieved later to find out what objects were encountered, i.e. in a TPM. Measured Boot doesn’t make an implicit value judgment as to good or bad, and it doesn’t stop the platform from running, so Measured Boot can be much more liberal about what it checks. This can include all kinds of platform configuration information such as which was the boot device, what was in the loader configuration file, or anything else that might be of interest. Note that all UEFI BIOS’s should measure certain objects and store values in a TPM if enabled.
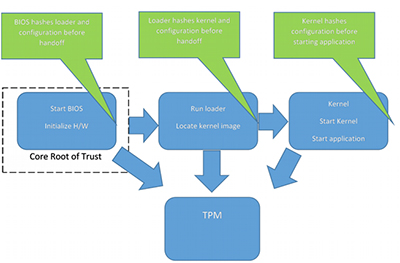
Figure: Measured Boot process
Once the values, stored in Platform Configuration Registers (PCR) have been collected, the next step is for the TPM to report the values, signed by a key that only the TPM can access. The resulting data structure, called a Quote, gives the PCR values and a signature, allowing them to be sent to a Remote Attestation server via an untrusted channel. The server can examine the PCRs and associated logs to determine if the platform is running an acceptable image.
Which boot process to use?
This will ultimately come down to customer requirements. Do you want to halt the boot process if an anomaly is detected? Is the equipment networked so that remote attestation can be carried out?
The ultimate secure boot process would be to use Boot Guard (assuming the processor/BIOS vendor supports it), a Secure Boot enabled UEFI BIOS, with a signed kernel/OS/application, and encrypted partition(s) on a drive that uses software to seal/unseal it with values stored in a TPM. Thus locking the system down to the current hardware/software/configuration build.
The next level down would be to do without Boot Guard, so Secure Boot enabled UEFI BIOS, with a signed kernel/OS/application, and an encrypted partition on a drive that uses software to seal/unseal it with values stored in a TPM.
If a boot loader/manager is required then this should be signed so that the UEFI Secure Boot can ensure it is a valid image. Customers could customize their own loader to do disk decryption or use self-decrypting drives.
Another option is to use Measured/Verified Boot which allows the boot process to progress without stopping but requires remote attestation software to check all is as expected.
For further information there is an Application Note (AN07x_Public_Secure_Boot) that gives one example of secure Boot on a Concurrent Technologies' VPX card and includes a trivial boot loader example that is signed and uses a TPM for storing/checking measurements.
Concurrent Technologies is an international ISO 9001:2015 company specializing in the design and manufacture of commercial-off-the-shelf and custom designed industrial computer boards for critical embedded applications. The company, which was founded in 1985, has sales offices in the USA, UK and China as well as a worldwide distributor network. The company has a wide range of high performance Intel® processor based VME, VPX, CompactPCI® and AdvancedMC™ products, which are complemented by an extensive offering of XMC (Express Mezzanine Card) products. Concurrent Technologies is an Affiliate Member of the Intel® Internet of Things Solutions Alliance.